This article delves into understanding ransomware, its various types, and provides a comprehensive guide on how to decrypt encrypted files, including real-world cases of successful decryption.
What is ransomware?
Ransomware is a type of malicious software that applies encryption to make a victim’s files inaccessible and holds them for ransom, typically payable in cryptocurrency. The primary motivation behind such attacks is monetary profit.
The operational methodology of ransomware is both simplistic in its approach and potent in its execution. Commonly, the adversary disseminates a phishing email embedded with a seemingly benign link or attachment. When the recipient, often unsuspectingly, interacts with the embedded content, the ransomware payload is delivered and activated on the host system. Subsequently, the encryption phase commences, potentially immobilizing individual files or entire system infrastructures.
The ramifications of a ransomware incident are multifaceted and can have profound implications. For individual entities, such an attack can culminate in the loss of personal and invaluable data, encompassing photographs, personal documents, and pivotal data like financial records. The emotional and financial toll of such a breach can be significant.

Conversely, commercial entities confronted with ransomware face amplified challenges. Operational functionalities can be entirely disrupted, translating to considerable economic setbacks. Beyond the immediate operational hindrance, enterprises are at risk of data breaches, which can tarnish their reputation. The recuperation process, both financially and in terms of stakeholder trust, is often extensive. Moreover, legal ramifications may arise, especially if the breach compromises sensitive client or customer data.
In a broader perspective, the fallout from a ransomware incident transcends the mere immediate data loss. Its cascading effects permeate the emotional, fiscal, and operational dimensions of both individual and corporate victims.
Types of ransomware
Ransomware has evolved over the years, leading to the emergence of various types, each with its unique characteristics:
Crypto ransomware
This type of ransomware encrypts valuable files on a victim’s computer.
Examples:
- WannaCry: Targeted Windows systems using the EternalBlue vulnerability.
- LockBit: afflicted such giants as Bangkok Airways and Accenture over few weeks.
- Petya/NotPetya: Disguised as ransomware, its main purpose was to cause disruption, especially in Ukrainian businesses.
Locker ransomware
Instead of encrypting files, locker ransomware locks the victim out of their device, demanding a ransom to unlock it.
Example:
- WinLocker: Presents itself as a Windows update, then locks the user out, demanding payment.
Doxware (or leakware)
This type threatens to publish the victim’s stolen information unless a ransom is paid.
Example:
- Popcorn Time: Besides encrypting data, it offers victims an alternative to paying: infecting two other users.
RaaS (Ransomware as a Service)
A model where cybercriminals rent out ransomware infrastructure to other criminals, taking a cut from the profits.
Example:
- GandCrab: Operated as RaaS, it rapidly evolved and had multiple versions before its alleged retirement.
Scareware
A form of malware that tricks victims into thinking their computer has a virus. The attacker then offers a solution for a fee.
Example:
- FakeAV: Misleads users into believing their system is infected, prompting them to purchase fake antivirus software.
Steps to decrypt ransomware encrypted files
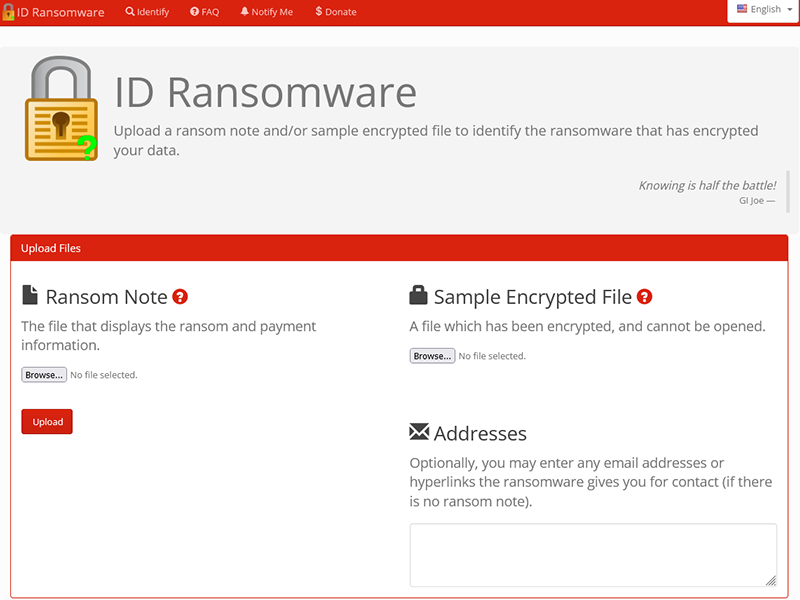
Identifying the ransomware type
Before attempting any decryption, it’s crucial to identify the specific type of ransomware affecting your files. Several online platforms, like ID Ransomware, can assist users in pinpointing the ransomware variant.
Using decryption tools
Once the ransomware type is identified, users can search for specific decryption tools tailored for that variant. Several cybersecurity firms and organizations offer free decryption tools. Some of the most notable ones include:
- No More Ransom’s decryption tools: Initiated as a joint venture between cybersecurity entities and law enforcement agencies, No More Ransom furnishes an extensive array of complimentary decryption solutions tailored for diverse ransomware variants. Their online platform disseminates guidelines and best practices for preemptive measures against ransomware threats.
- Emsisoft’s free decryptors: Emsisoft has a dedicated section for ransomware decryption tools. They’ve developed solutions for ransomware families like MRCR (Merry X-Mas), Cry9, and Damage.
- Bitdefender’s ransomware recognition tool: Bitdefender offers a tool that helps victims identify the type of ransomware affecting their files. Once identified, users can then download the appropriate decryption tool from Bitdefender’s extensive list.
- Trend Micro’s Ransomware File Decryptor: Trend Micro provides a free tool designed to decrypt files encrypted by certain ransomware families. Their tool supports a variety of ransomware, including CryptXXX v1, v2, v3, and SNSLocker.
- Avast’s decryption tools: Avast has developed a series of decryption tools for ransomware variants such as Alcatraz Locker, Apocalypse, and BadBlock.
- McAfee’s ransomware decryptors: McAfee, another giant in the cybersecurity industry, offers tools to decrypt files affected by ransomware families like GandCrab, Petya, and TeslaCrypt.
- Kaspersky’s ransomware decryptors: Kaspersky Lab has been at the forefront of the battle against ransomware. They offer a range of decryptors for different ransomware families, including CoinVault, Rakhni, and Rannoh.
Restoring from backups
If you’ve been proactive and have backups of your data, restoring your system becomes a viable option. However, it’s essential to ensure that the backup itself isn’t compromised or infected with ransomware.
Real-world cases of successful decryption
TeslaCrypt ransomware
In a surprising turn of events, the developers of TeslaCrypt shut down their operations and released the master decryption key. Cybersecurity researchers quickly utilized this key to develop decryption tools, aiding victims in retrieving their encrypted files.
WannaCry ransomware
In 2017, the ransomware variant known as WannaCry compromised in excess of 200,000 computing systems spanning 150 nations. Subsequent to the outbreak, a cybersecurity researcher fortuitously identified a “kill switch” embedded within the ransomware’s code. This discovery played a pivotal role in halting the malware’s propagation and facilitated the creation of decryption utilities for the impacted data sets.
GandCrab ransomware
GandCrab, one of the most prolific ransomware families, saw its reign end when cybersecurity firms and law enforcement agencies collaborated to release free decryption tools. These tools helped thousands of victims recover their data without paying a ransom.
Preventing future ransomware incidents
Though decryption serves as a post-incident response, a more strategic approach to ransomware emphasizes preemptive measures. Below are recommended actions to enhance resilience against potential ransomware threats:
Regular backups
Consistently back up your data. Utilize both cloud storage and physical storage devices to ensure redundancy. Automated backup systems can also be set up to run at regular intervals, ensuring that your most recent data is always safe.
Updated security software
Regularly update your antivirus software to protect against the latest threats. Additionally, consider investing in specialized anti-ransomware tools that offer real-time protection against ransomware attacks.
Educating yourself and others
Knowledge is power. Stay informed about the latest ransomware threats and their modus operandi. Regularly attend cybersecurity workshops, webinars, or training sessions. Additionally, spread awareness and educate your peers, family, and colleagues about the dangers of ransomware and the importance of cybersecurity hygiene.
In summary, ransomware represents a significant challenge within the cybersecurity landscape. By leveraging appropriate knowledge, utilizing advanced tools, and adopting best practices, both individuals and enterprises can effectively mitigate the risks associated with this cyber threat. It is imperative to emphasize proactive strategies over reactive responses in cybersecurity, underscoring the principle that constant vigilance remains the most effective line of defense.